一、 漏洞 CVE-2025-29781 基础信息
漏洞标题
漏洞描述信息
CVSS信息
漏洞类别
漏洞标题
漏洞描述信息
CVSS信息
漏洞类别
漏洞标题
漏洞描述信息
CVSS信息
漏洞类别
二、漏洞 CVE-2025-29781 的公开POC
| # | POC 描述 | 源链接 | 神龙链接 |
|---|
三、漏洞 CVE-2025-29781 的情报信息
-
标题: :warning: Only accept HTTPHeadersRef in same namespace by tuminoid · Pull Request #2321 · metal3-io/baremetal-operator · GitHub -- 🔗来源链接
标签: x_refsource_MISC
-
标题: :warning: Only accept HTTPHeadersRef in same namespace by tuminoid · Pull Request #2322 · metal3-io/baremetal-operator · GitHub -- 🔗来源链接
标签: x_refsource_MISC
-
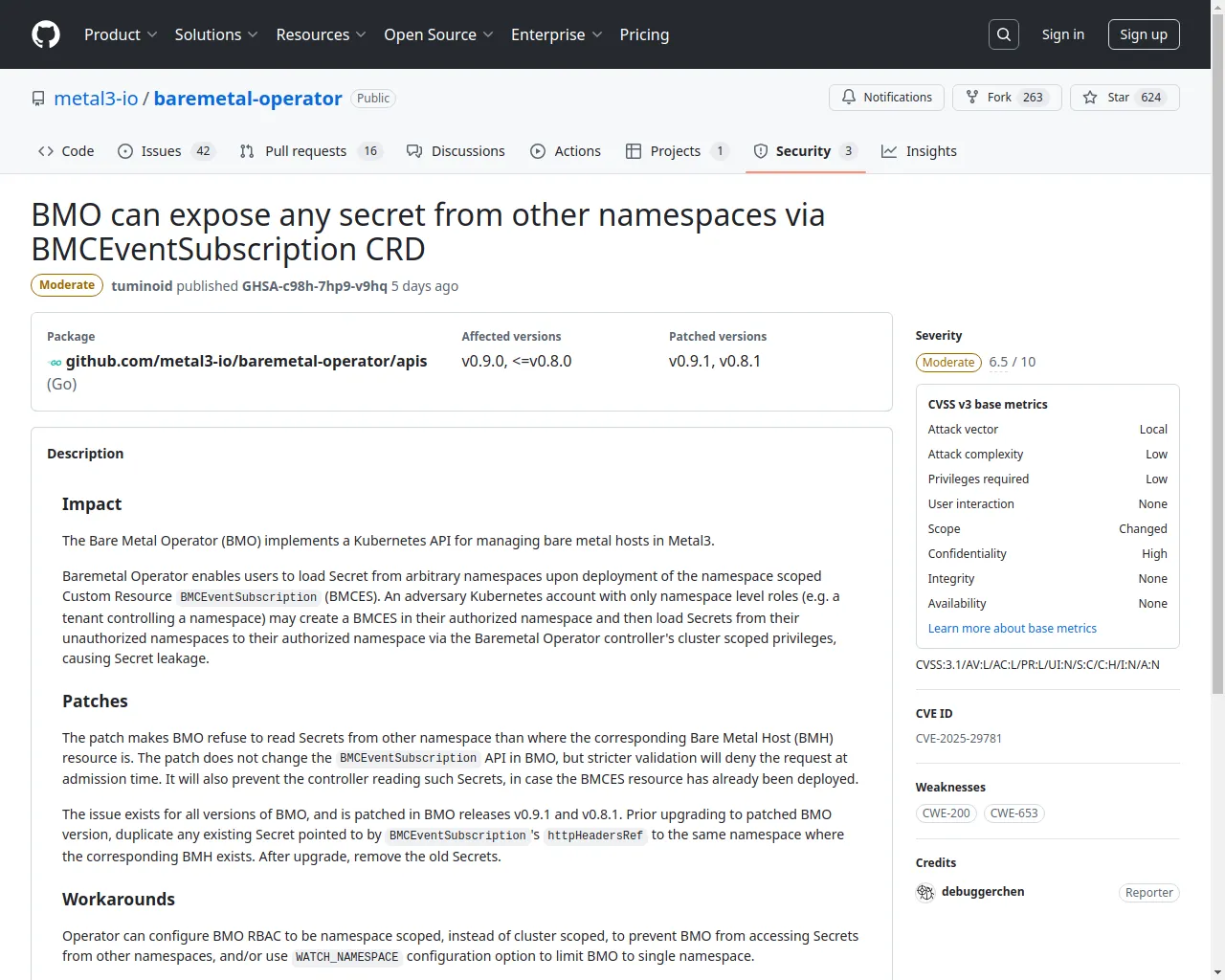
标题: BMO can expose any secret from other namespaces via BMCEventSubscription CRD · Advisory · metal3-io/baremetal-operator · GitHub -- 🔗来源链接
标签: x_refsource_CONFIRM
-
标题: metal3-docs/design/baremetal-operator/bmc-events.md at main · metal3-io/metal3-docs · GitHub -- 🔗来源链接
标签: x_refsource_MISC
-
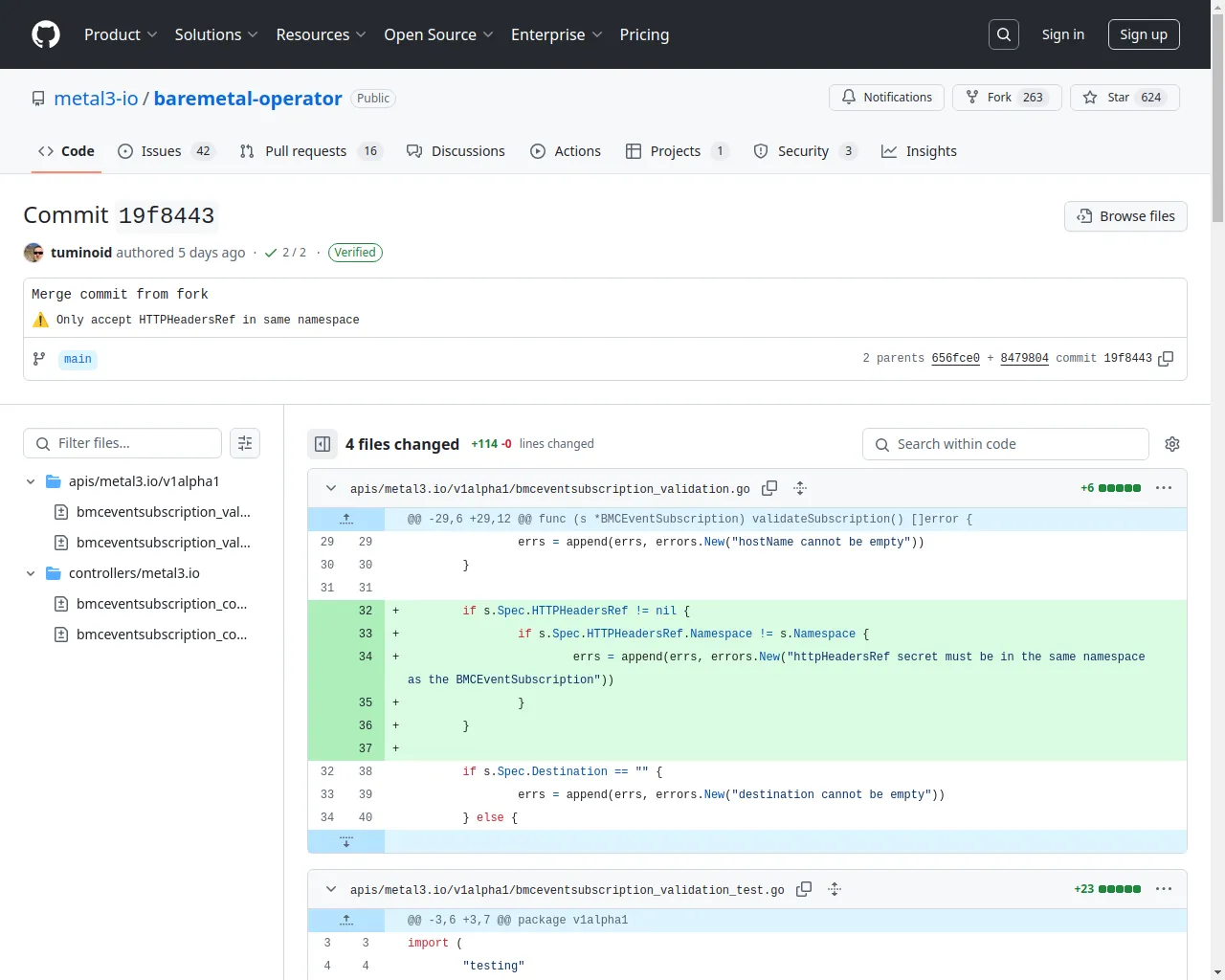
标题: Merge commit from fork · metal3-io/baremetal-operator@19f8443 · GitHub -- 🔗来源链接
标签: x_refsource_MISC
- https://nvd.nist.gov/vuln/detail/CVE-2025-29781