一、 漏洞 CVE-2025-31491 基础信息
漏洞标题
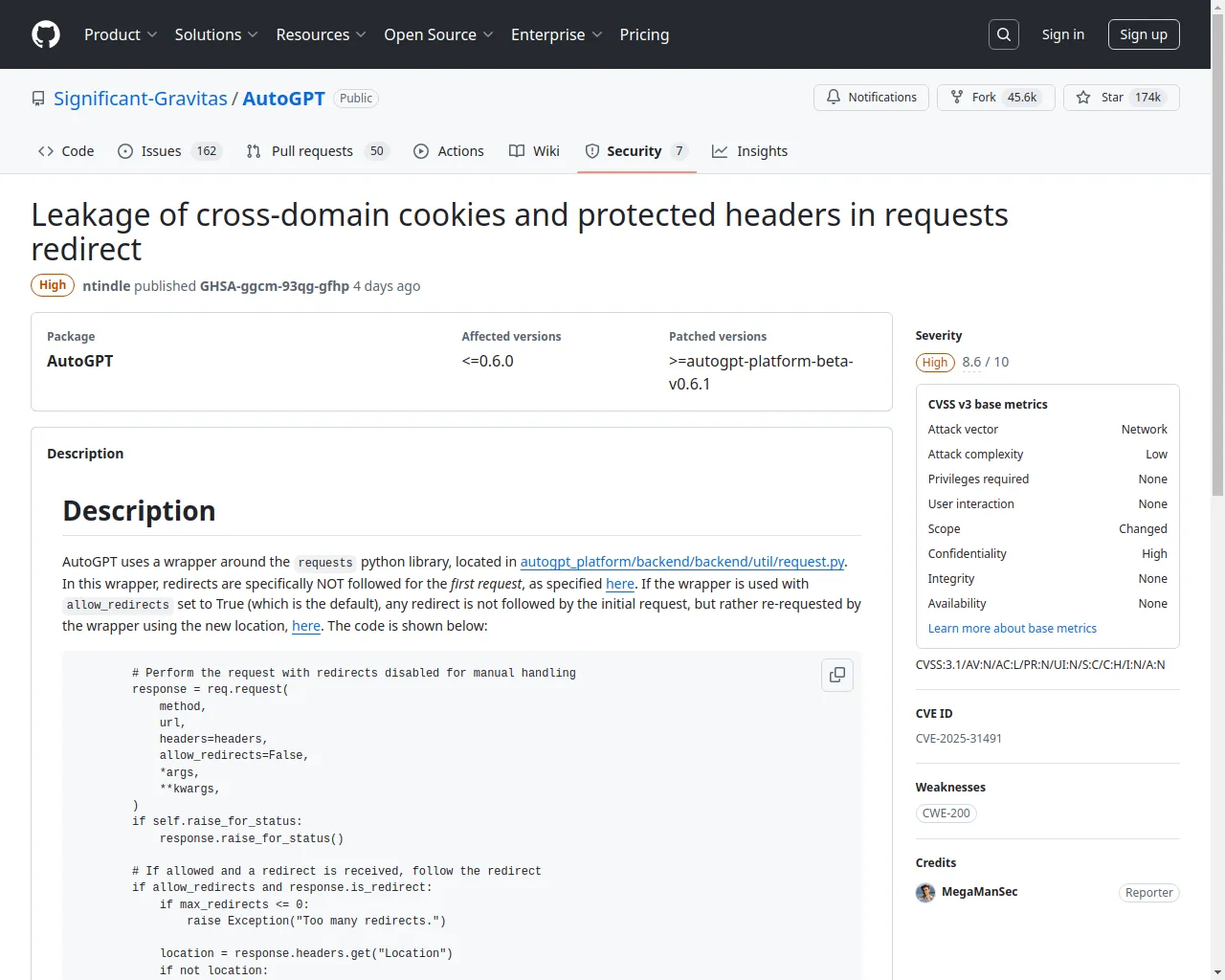
AutoGPT 允许在请求重定向中泄露跨域 cookie 和受保护的标头
来源:AIGC 神龙大模型
漏洞描述信息
N/A
来源:AIGC 神龙大模型
CVSS信息
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:N/A:N
来源:AIGC 神龙大模型
漏洞类别
指向未可信站点的URL重定向(开放重定向)
来源:AIGC 神龙大模型
漏洞标题
AutoGPT allows leakage of cross-domain cookies and protected headers in requests redirect
来源:美国国家漏洞数据库 NVD
漏洞描述信息
AutoGPT is a platform that allows users to create, deploy, and manage continuous artificial intelligence agents that automate complex workflows. Prior to 0.6.1, AutoGPT allows of leakage of cross-domain cookies and protected headers in requests redirect. AutoGPT uses a wrapper around the requests python library, located in autogpt_platform/backend/backend/util/request.py. In this wrapper, redirects are specifically NOT followed for the first request. If the wrapper is used with allow_redirects set to True (which is the default), any redirect is not followed by the initial request, but rather re-requested by the wrapper using the new location. However, there is a fundamental flaw in manually re-requesting the new location: it does not account for security-sensitive headers which should not be sent cross-origin, such as the Authorization and Proxy-Authorization header, and cookies. For example in autogpt_platform/backend/backend/blocks/github/_api.py, an Authorization header is set when retrieving data from the GitHub API. However, if GitHub suffers from an open redirect vulnerability (such as the made-up example of https://api.github.com/repos/{owner}/{repo}/issues/comments/{comment_id}/../../../../../redirect/?url=https://joshua.hu/), and the script can be coerced into visiting it with the Authorization header, the GitHub credentials in the Authorization header will be leaked. This allows leaking auth headers and private cookies. This vulnerability is fixed in 0.6.1.
来源:美国国家漏洞数据库 NVD
CVSS信息
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N
来源:美国国家漏洞数据库 NVD
漏洞类别
信息暴露
来源:美国国家漏洞数据库 NVD
漏洞标题
AutoGPT 信息泄露漏洞
来源:中国国家信息安全漏洞库 CNNVD
漏洞描述信息
AutoGPT是AutoGPT开源的一个工具。用于让每个人都能使用和构建可访问的AI。 AutoGPT 0.6.1之前版本存在信息泄露漏洞,该漏洞源于请求重定向中存在跨域cookie和受保护标头泄露问题。
来源:中国国家信息安全漏洞库 CNNVD
CVSS信息
N/A
来源:中国国家信息安全漏洞库 CNNVD
漏洞类别
信息泄露
来源:中国国家信息安全漏洞库 CNNVD
二、漏洞 CVE-2025-31491 的公开POC
| # | POC 描述 | 源链接 | 神龙链接 |
|---|
三、漏洞 CVE-2025-31491 的情报信息
-
标题: Leakage of cross-domain cookies and protected headers in requests redirect · Advisory · Significant-Gravitas/AutoGPT · GitHub -- 🔗来源链接
标签: x_refsource_CONFIRM
- https://nvd.nist.gov/vuln/detail/CVE-2025-31491