关联漏洞
标题:
Episerver Ektron CMS 安全漏洞
(CVE-2018-12596)
描述:Episerver Ektron CMS是瑞典EPiServer公司的一套内容管理系统(CMS)。 Episerver Ektron CMS 9.0 SP3 Site CU 31之前版本,SP3 Site CU 45之前的9.1版本,或SP2 Site CU 22之前的9.2版本中的“activateuser.aspx”页面存在安全漏洞。远程攻击者可利用该漏洞启用用户账户。
描述
Ektron Content Management System (CMS) 9.20 SP2, remote re-enabling users (CVE-2018–12596)
介绍
# CVE-2018-12596
Ektron CMS 9.20 SP2 allows remote attackers to call aspx pages via the "activateuser.aspx" page, even if a page
is located under the /WorkArea/ path, which is forbidden (normally available exclusively for local admins).
Exploit-DB publication at https://www.exploit-db.com/exploits/45577/ </br>
PacketStorm publication at https://packetstormsecurity.com/files/149734/Ektron-CMS-9.20-SP2-Improper-Access-Restrictions.html
# Timeline
================</br>
2018–06–08: Discovered </br>
2018–06–11: Retest staging environment </br>
2018–06–12: Restes live environment </br>
2018–06–19: Internal communication </br>
2018–06–21: Vendor notification </br>
2018–06–21: Vendor feedback </br>
2018–06–29: Vendor feedback product will be patched </br>
2018–06–29: Patch available </br>
2018–06–29: Agrements with the vendor to publish the CVE/Advisory </br>
2018–07–30: Internal communication </br>
2018–09–15: Patches tested on LAB environment <br>
2018–10–08: Public report <br>
# Episerver (Ektron Product 9.20 SP2) Patch and credits:
https://support.episerver.com/hc/en-us/articles/115002828112-9-2-SP2-Site-Update
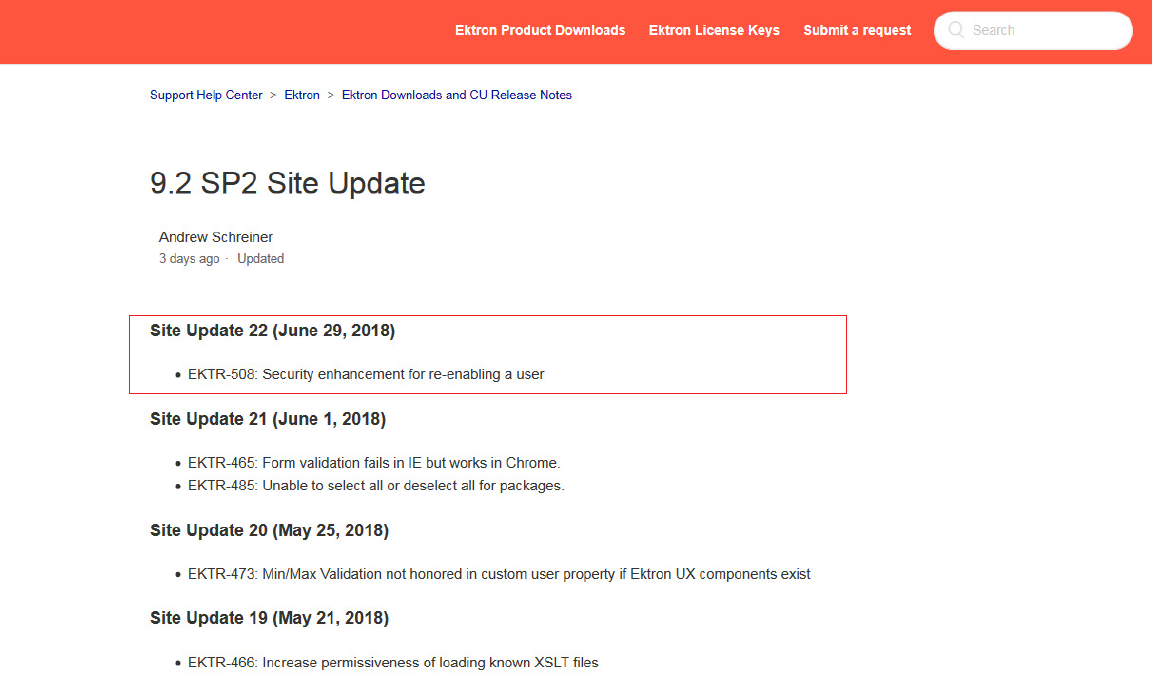
# Author
Alex Hernandez aka <em><a href="https://twitter.com/_alt3kx_" rel="nofollow">(@\_alt3kx\_)</a></em><br>
My current exploit list @exploit-db: https://www.exploit-db.com/author/?a=1074 <br>
CVE-2018-12596 with sexy screens here: https://medium.com/@alt3kx
文件快照
[4.0K] /data/pocs/255cf935f73f5d0cef15e7d2dc1efb0869f7aa56
├── [3.6K] CVE-2018-12596.txt
├── [ 34K] LICENSE
└── [1.5K] README.md
0 directories, 3 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。